Recapitulation
The second edition of the Open Security Conference brought together 39 participants for a weekend of collaboration, hands-on learning, and community-driven security exploration. osco 2025 continued its mission of making cybersecurity accessible for everyone, welcoming newcomers, seasoned professionals, researchers, defenders, attackers, and engineers in an inclusive and safe space. The open space format empowered participants to shape the conference together, fostering shared learning, deep technical discussions, spontaneous workshops, and meaningful personal connections.
Participant Experience
Feedback throughout the weekend highlighted strong themes of belonging, inclusion, and shared curiosity. Many participants expressed how special it felt to be part of a space where all experience levels were appreciated, where it was easy to connect with almost everyone, and where the organizers built an environment that was supportive, open, and welcoming. The scale of the group created a rare intimacy that led to authentic conversations, deep learning, and real friendships. Several people referred to osco repeatedly as a magical place to be.
The atmosphere, openness, and thoughtful design elements — such as sunflower indicators for hidden disabilities and communication cards for neurodiverse support — stood out as meaningful contributions to inclusion. Participants noted that these gestures reflected not only awareness but care, and shaped how comfortable they felt participating.
Talks and Sessions
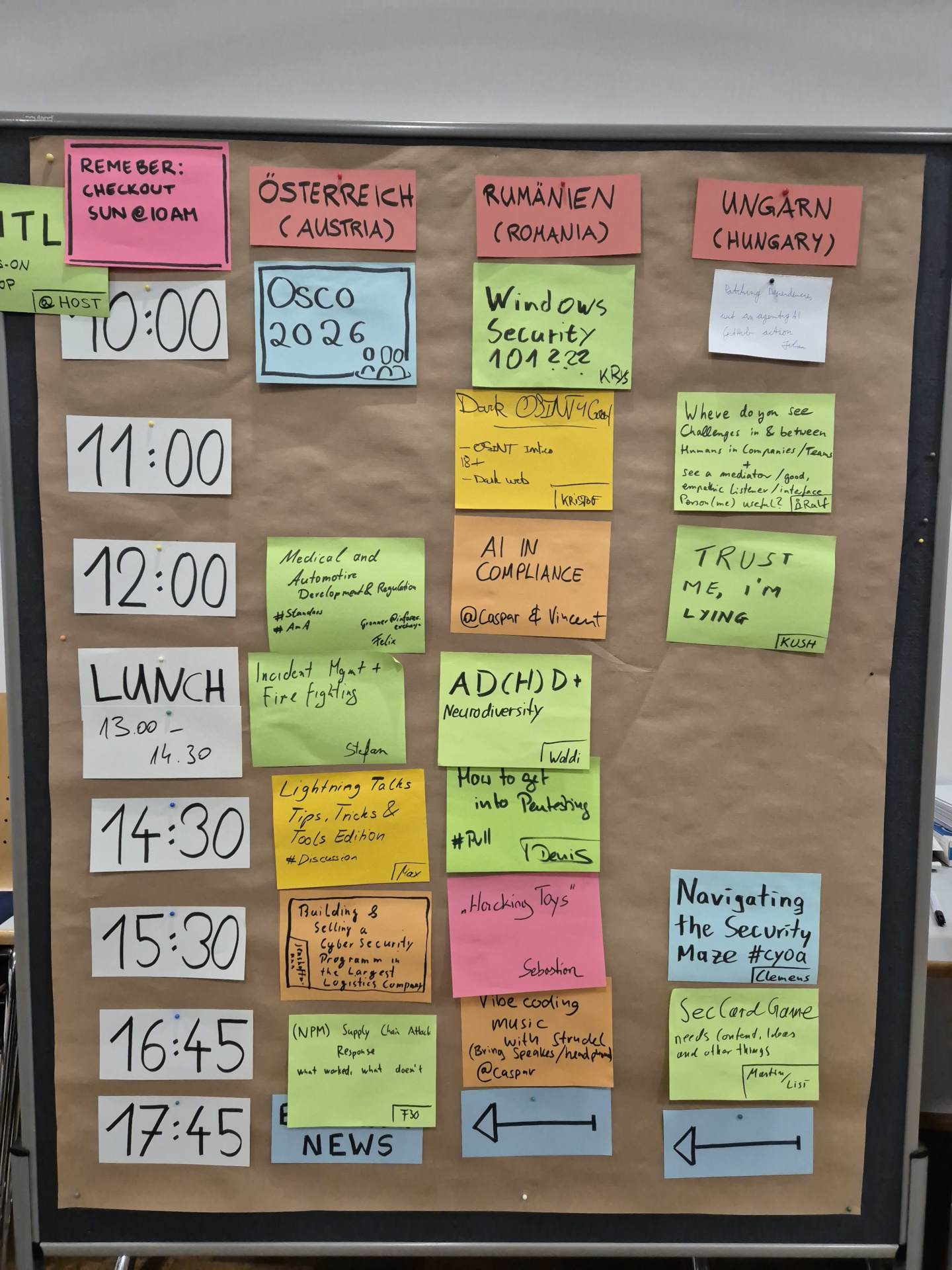
Because osco uses an open space format, the schedule emerged dynamically each morning as participants proposed sessions, workshops, and conversations. What followed was a rich and diverse set of contributions spanning practical security, offensive techniques, defensive strategy, culture, and collaboration. Let’s dive into a choice selection of the sessions.
The first evening kicked off with Mireia’s keynote, Building an AppSec Program from Scratch, which explored the foundations of establishing a Security Champion program inside a company. The talk resonated with many attendees navigating similar journeys, and the open sharing of challenges and lessons learned set a strong tone for honesty and vulnerability throughout the conference.
Day one opened with a packed marketplace of proposals and the immediate realization that there were more compelling sessions than time would allow. Among the first selections was the Juice Shop CTF session led by Julian, who walked participants through solving a real challenge from the OWASP Juice Shop project. It became a collaborative hacking workshop, with participants exploring vulnerabilities together and helping each other progress.
Felix followed with an introduction to Threagile and pytm, demonstrating threat modeling approaches and tools. The session sparked lively discussion on practical modeling methods and directly led some attendees to order the threat modeling card decks for use at work. Clemens later expanded on the topic with a hands-on round of Cornucopia and Cumulus thread modeling card games, creating an unexpectedly interactive and energetic learning experience.
Lock-picking surfaced as a recurring favorite, with Denis leading an impromptu workshop supported by participant-brought training locks and kits. This session continued informally into the bar later that evening, where people gathered around tables solving physical security challenges together.
Matthias hosted a session on Product Security Assessment Basics, diving into the realities of documenting risks, compliance requirements, and trade-offs between security and business constraints. The conversation touched on decision-making transparency, audit trails, and the practical obstacles that exist in real environments.
The evening keynote, Bianca Kastl’s History Repeating Itself, examined patterns in security failures across decades and challenged the audience to reflect on why certain mistakes persist despite accumulated knowledge. It was a sobering but motivating reminder of the importance of shared context and ongoing community.
Day two expanded even further, starting with Windows Security 101 by Krys, during which participants launched the Hack The Box Active Directory track. Kristof’s talk on Dark OSINT explored humanitarian OSINT projects and gave insight into how open-source intelligence is used in real-world scenarios to help protect vulnerable individuals. Another standout talk, Trust Me, I’m Lying by Kush, introduced OODA loops and deception strategies to slow or mislead attackers, blending psychology with security practice.
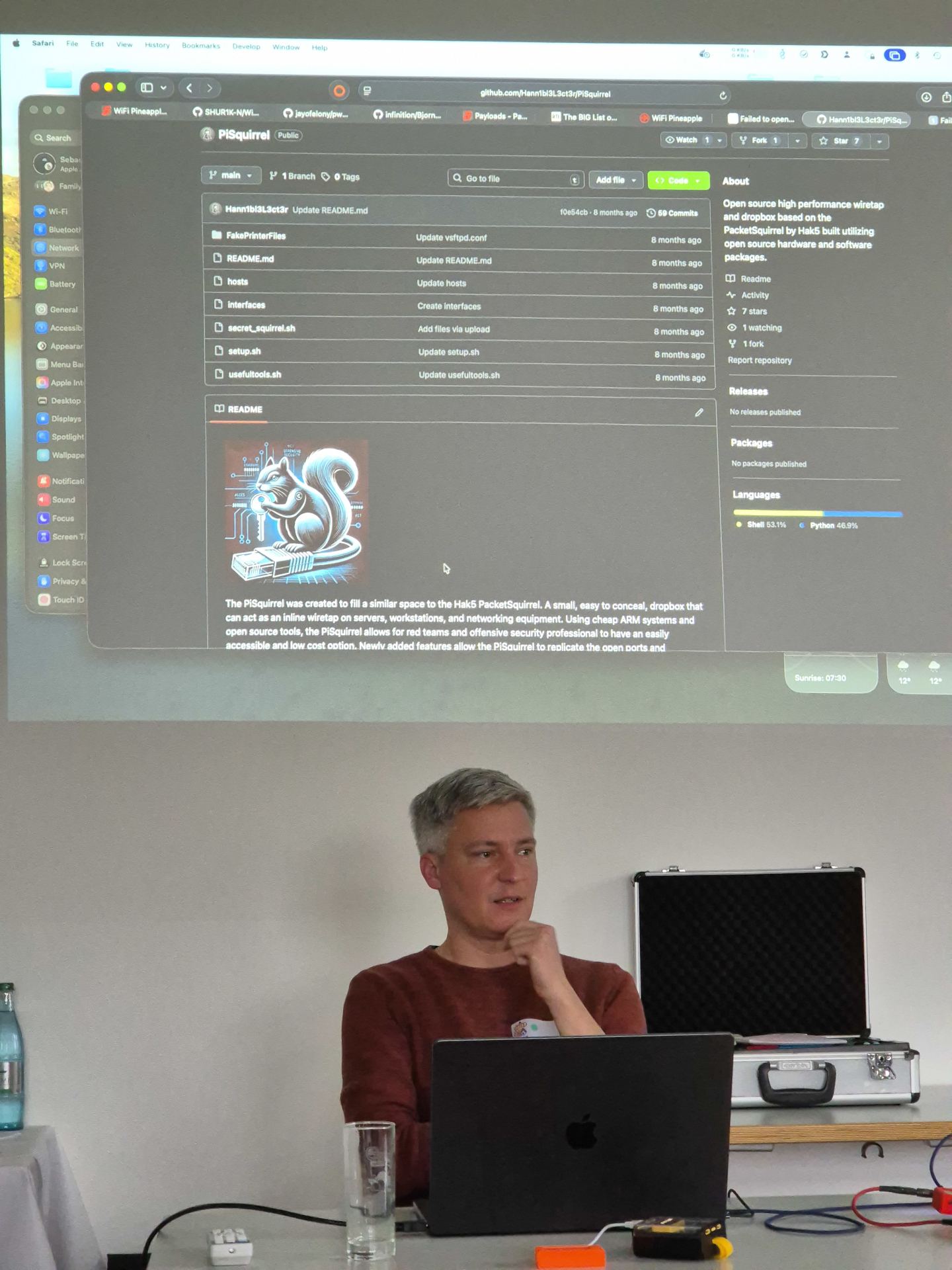
Denis and Kristof hosted a session on How to get into PenTesting, offering guidance on certifications such as OSCP and HTB CPTS, as well as practical bug bounty advice. Sebastian presented real hacking tools for network intrusion, including pwnagotchi and PiSquirrel, which generated excitement and follow-up experimentation.
This second day of open space also showed how all kinds of sessions are relevant to participants and that they have a place at osco. Waldi initiated a conversation on AD(H)D + Neurodiversity over lunch, and they attracted many interested folks with it, the session was packed. Anne inspired people to go outside and enjoy flying kites together which was gladly picked up by people as well. Same goes for evening sessions which were going strong with several hacking challenges people worked on together, games being played in the bar, and people generally enjoying their time among peers.
Day three closed with Lisi’s workshop Secure Development Lifecycle Applied, which provided hands-on exercises around improving systems incrementally and included threat modeling, secure coding principles applied, testing for vulnerabilities and how to spot malicious activity on production. This session captured the spirit of osco — collaborative, practical, and deeply human.
Areas to Improve and Opportunities Ahead
Participants offered thoughtful and constructive feedback: clearer communication around schedule changes, expanded vegan food options, printed timelines for session navigation, better transparency around included costs, and more channels for staying connected after the event. Suggestions such as a Signal group, participant-shared photo space, printed sticker legends, and solidarity ticket options for accessibility have already been captured for planning osco 2026.
Growth and the Future
osco 2025 nearly doubled in size from the previous year, growing to 39 participants, an increase of 95 percent. The growth validates the belief that conferences focused on community, inclusion, and curiosity hold meaningful value. Because of the overwhelmingly positive response, osco 2026 is already confirmed to take place on November 5 - 8; save the date!
A Final Thank You
Thank you to everyone who attended, shared knowledge, asked questions, mentored others, and helped create a warm and inspiring environment. You made osco 2025 what it was.
See You at osco 2026
Search the hashtags #osco26 and #osco on Mastodon, LinkedIn and Bluesky for reflections from participants and additional articles, and follow for news.
Gallery
Here are some pictures from the conference to give you an idea of what it was like.